Hyper MZT Privacy Policy
Welcome to use the services provided by Hyper MZT! Xi 'an Diance Network Technology Co., LTD. (hereinafter referred to as "we") attaches great importance to the protection of your privacy and personal information. Hyper MZT Privacy Policy (hereinafter referred to as "this Agreement") applies to your use of Hyper MZT services in various ways, including multiple application versions of Hyper MZT such as IOS and Android, and smart devices equipped with Hyper MZT.
You may use Hyper MZT for device connection, live recording, simultaneous interpretation, face-to-face translation, audio and video calls, AI assistants, etc. (collectively referred to as "Hyper MZT products or services"). We will only process the personal information you need to use the products or services.
This agreement is intended to help you understand what personal information we collect, why we collect it, what we do with it and how we protect it. We will collect and use your personal information in accordance with our privacy Policy, but we will not collect all of your personal information in a mandatory bundle manner merely because you have authorized and agreed to this agreement. We will seek your separate consent strictly in accordance with the requirements of laws and regulations in certain circumstances. In addition to this agreement, we may also inform you of our rules for processing your personal information through product page notifications, pop-up prompts, etc. The processing of personal information corresponding to specific business functions shall be subject to specific rules, which have the same effect as this agreement.
Unless otherwise provided by law or administrative regulations, you have the right to know and to decide how we handle your personal information, and to restrict or refuse us or other parties from processing your personal information; At the same time, you have the right to request us to explain the rules we provide to you regarding the processing of your personal information. Please read and understand this agreement carefully before using Hyper MZT-related products and services in order to make appropriate choices.
This agreement will help you understand the following:
1. The information we collect and the purposes for which it is used
2. How do we share, transfer and publicly disclose your personal information
3. How do we keep and protect your personal information
4. Your Rights
5. Third-party SDK
6. How do we handle personal information of minors
7. How is this agreement updated
8. How to Contact Us
We are well aware of the importance of your personal information and that providing effective protection for your information is the cornerstone of the healthy and sustainable development of our business. Thank you for your use and trust in Hyper MZT! We are committed to maintaining your trust in us by the following principles to protect your personal information: the principle of consistency of rights and responsibilities, the principle of clear purpose, the principle of consent, the principle of minimum sufficiency, the principle of security, the principle of subject participation, the principle of openness and transparency, etc. We solemnly commit that we will take corresponding security protection measures in accordance with mature security standards in the industry to protect your personal information. We will take corresponding security measures to protect your personal information in accordance with established industry security standards.
1. The information we collect and the purposes for which it is used
We will collect and use your personal information in accordance with the principles of legality, propriety and necessity. Specifically, we collect and process your personal information for the purpose of providing you with the corresponding business functions. In the corresponding functions, if you provide personal information of someone else, please ensure that you have obtained the authorization of the relevant entity. We reserve the right to verify the legal source of such personal information at any time.
You need to provide us with personal information in order for us to perform the basic business functions of Hyper MZT. The information necessary for the basic business function is essential personal information. If you refuse to provide this essential personal information, we will not be able to provide you with the basic business function and the corresponding service. In addition to the basic business functions, you may choose to provide us with some of your personal information to enable us to implement the extended business functions of Hyper MZT. We will inform you of the purpose of use and process this personal information based on your authorized consent or for the purposes necessary to achieve the extended business functions of your choice. Your refusal to provide such extended business function information will not affect your use of our basic business function, but if you refuse to provide the personal information necessary for the extended business function, we will not be able to provide you with the extended business function.
For your convenience, we list the business functions we provide, the purposes for which they are processed and the personal information required for them as follows:
Description of the information collection function
(a) equipment information, packet contains: equipment serial number, IMEI, AndroidID, OAID, GAID, MAC address, installed APP information, the only equipment used for account registration binding, the binding of user members' rights and interests;
(b) Storage permissions for saving and displaying user information, caching error messages, etc.
(c) Access to network connections may generate GPRS traffic;
(d) Obtain network information status for alerting users to data consumption;
(e) Voice permissions for user voice recognition and voice communication;
(f) Location permission for ble scanning of nearby Bluetooth devices to obtain recording location information;
(g) Bluetooth permission for nearby Bluetooth device ble scan, connection;
(h) Acceleration sensor for video call status to obtain the phone's horizontal or vertical screen status to fit the direction of the captured image;
1.1 Register and log in to your account
Packet contains: equipment serial number, IMEI, AndroidID, OAID, GAID, MAC address, installed APP information, the only equipment used for account registration binding, user membership rights and interests of the binding, you can through the mobile phone number to create the Hyper MZT account, and you can complete your account information. When you register and log in to your Hyper MZT account, you need to provide us with your mobile phone number or email account.
1.2 Provide you with intelligent voice service
When you activate a specific feature of the Hyper MZT program, we will automatically receive and record relevant information (including appropriate environmental parameters such as noise indicators) generated during your interaction with the device terminal for the purpose of providing you with services. Note that if the program's wake-up function is on, Hyper MZT will wake up when it receives the wake-up action, and we will only collect voice information after receiving the wake-up action. If you refuse us to collect the above information, please turn off the information collection function of your device or do not wake up the device, but this will also result in you not being able to receive the relevant service.
In order to provide you with the functions of voice recognition and conversation, we need to collect the voice information you input and the device identifier. If you do not provide such information, voice recognition and text input cannot be performed through Hyper MZT.
When you use Hyper MZT's intelligent voice interaction feature, you can interact with Hyper MZT through voice input. At this point, we will request your microphone permission and collect your voice message (only for text-to-text processing), delete it immediately after processing, and do not retain it. We will automatically receive and record the text conversation information converted from your voice during your interaction with Hyper MZT, and use this information to output content to you to provide human-computer interaction services. At the same time, we will store the aforementioned text conversation information for your subsequent query. If you refuse our collection and processing of the aforementioned personal information, please enter the aforementioned information with caution, but this may affect your normal use of the aforementioned functions.
1.3 Smart Device connection and control
We collect information about your device in order to provide more tailored services for different device terminals.
To ensure that we provide services to you normally, we will collect MAC addresses of your mobile phone, smart devices, device Bluetooth, WiFi, network card in the background to enable you to connect and manage smart devices and Bluetooth devices securely. In addition, in the background, we will also collect your IMEI information for daily active data statistics.
When you use the [Conference recording, simultaneous interpretation, face-to-face Translation] function of the smart headset, we will request access to the microphone and recording permission to collect your voice input for the purpose of voice-to-text, recording and translation. We encrypt the transmission and processing of your voice input and delete it immediately after the purpose of use is achieved to ensure the security of the data and prevent it from being used for other purposes.
1.4 New service and feature operations and customer service handling
If you participate in related operational activities, we may collect your identity information and contact details through the operational activity interface in order to get in touch with you, send you operational rewards, etc. If you do not participate in the relevant operating activities, you will not be required to provide the aforementioned information.
In order to ensure call quality and that disputes are properly resolved, we may keep records of your communication with us, including call records, the information you provide related to your dispute resolution, and the contact information you use or provide.
1.5 Ensure service security, optimization and improvement of service purposes
When you use Hyper MZT, in order to ensure your normal use of Hyper MZT services, more accurately locate and solve the problems you encounter when using Hyper MZT services, improve and optimize the Hyper MZT service experience, and ensure the security of your account, We will collect your device information, location information, log information and other information related to the login environment to prevent, detect and investigate fraud, security hazards, illegal or violations of our agreement, policy or rule, in order to protect the legitimate rights and interests of you, us or our affiliates, partners and the general public.
Please understand that when you switch Hyper MZT from your device screen to running in the background, due to some device models and system reasons, the information collection behavior that you previously used Hyper MZT-related functions may not be immediately stopped, resulting in a brief background information collection behavior.
1.6 Additional services provided to you
1.7 Additional features based on location information
When you use the location-based services provided by Hyper MZT, we may collect and process information about your device, location, and network identity information so that you can use the following services without manually entering your geographic coordinates. Location information includes precise location information obtained through GPS information, WLAN access points, Bluetooth, base stations and other sensor information, as well as rough geographical location information obtained through IP addresses or other network information. When you use the following features, we will request precise location permission authorization. If you refuse to grant precise location permission, we will not provide you with the above services based on the precise location information. We will only provide you with services based on the city and/or district information corresponding to the IP address or other network information and the rough location information inferred from the other network location information. Please be informed that the IP address information we use has been de-identified, and data analysis and inference correspond only to specific codes that do not directly relate to your identity and are not associated with your real information.
When you use the device add-on feature, we collect your location information to ensure that devices near you can be detected via Bluetooth.
You can cancel the system authorization for Hyper MZT to access your precise location information at any time, stop our collection of your precise geographical location information. After that, you may not be able to use the relevant services or functions provided based on the above precise location information, or fail to achieve the intended effect of the relevant services provided based on the above precise location information. But this will not affect your normal use of Hyper MZT's other business functions that are not based on precise location information.
1.8 Additional services based on the microphone:
When you use Hyper MZT products or services, you can enable microphone permission for recording, and we will collect your recordings and process the voice content for functional purposes. For voice messages and home broadcast, we will also collect the identifiers of the receiving devices for the purpose of sending and playing voice messages to the Hyper MZT you specify.
1.9 Exceptions to prior authorized consent
Note: In the following circumstances, the collection and use of your personal information do not require your prior authorization and consent:
Directly related to national security and defense security;
Necessary for the conclusion and performance of a contract in which an individual is a party;
Necessary for the performance of a statutory duty or obligation;
To respond to a public health emergency or to protect the life, health and property of a natural person in an emergency;
Relating directly to criminal investigation, prosecution, trial and enforcement of judgments;
Where it is necessary to protect your or another person's vital legitimate rights and interests, such as life and property, but it is difficult to obtain your consent;
Collect personal information that you have voluntarily disclosed to the public or that has been lawfully disclosed in accordance with laws and regulations within a reasonable scope;
Collect your personal information from legally disclosed information within a reasonable scope as required by laws and regulations, such as legitimate news reports, government information disclosure channels, etc.
Personal information is processed to a reasonable extent for the purpose of conducting news reporting, public opinion supervision, etc.;
Where it is necessary for an academic research institution to conduct statistics or academic research in the public interest and to provide the results of academic research or description to the public, and to de-identify the personal information contained in the results;
Other circumstances as prescribed by laws and regulations.
1.10 Anonymization of personal information
Without publicly disclosing or providing your personal information to others, we have the right to mine, analyze and utilize (including commercial use) the anonymized user database, to conduct statistics on the use of products/services and to share the anonymized statistical information with the public/third parties.
1.11 Device permission invocation
In the course of providing the service, in order to ensure that you can use the functions of the product normally, we will request the following system device permissions for your device from the system. Before applying, we will ask for your consent and you can choose to "allow" or "disable" the permission request. After your authorization, we will enable the relevant permissions. You can cancel the authorization in the system at any time. Your cancellation of the authorization will prevent you from using the relevant business functions, but will not prevent you from using other business functions.
When you use the Hyper MZT APP, we will invoke the privacy permissions of your mobile phone system as follows:
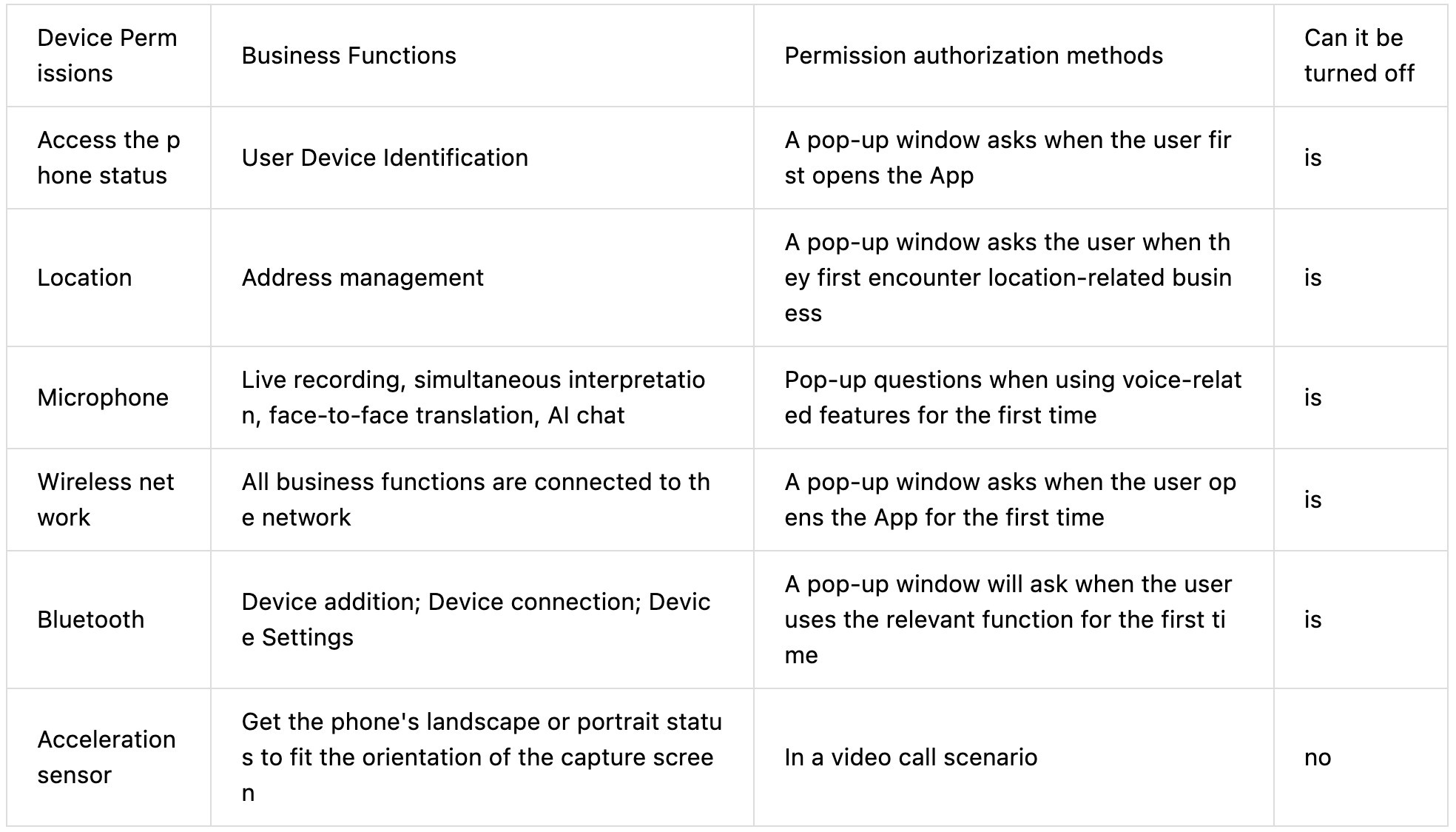
The display and disabling of permissions may vary across different devices. Please refer to the device and system developer's instructions or guidelines for details.
1.12 Other purposes that you have agreed to otherwise
We will seek your consent in advance if we want to use the information for any other purpose not specified herein. We will seek your consent in advance when we need to use information collected for a particular purpose for other purposes.
2 How do we share, transfer, publicly disclose, delegate processing of your personal information and access to third parties
Some of our services will be provided by authorized partners, and we may share certain of your personal information with partners only for the purposes stated in this agreement to provide better customer service and user experience. We will only share your personal information for legitimate, proper, necessary, specific and clear purposes, and only the personal information necessary to provide the services will be shared. Our partners have no right to use the shared personal information for any other purpose unless otherwise authorized by you or required by law.
2.1 Sharing
We will not share your personal information with any third party other than Xi 'an Diance Network Technology Co., Ltd. unless with your prior separate consent or as required by other laws and regulations, except where it has been processed to identify a specific individual and cannot be restored.
We will investigate the data security environment of the companies, organizations and individuals with whom we share personal information, sign strict confidentiality agreements with them, and require them to handle personal information in accordance with the confidentiality and security measures taken in accordance with the law.
We may share your personal information with the following third parties in the following circumstances:
2.1.1. Third-party product or service providers.
Hyper MZT integrates a wealth of third-party services (including third-party mini-programs). When you use third-party services connected to Hyper MZT, you may be required to submit your personal information. We will provide your personal information to the third party providing the service to you based on your valid authorization or if it is necessary for the conclusion and performance of a contract in which you are a party. Regarding exactly how third-party services collect and use your personal information, it is recommended that you refer to the relevant service agreements and privacy policies of third-party services.
When you participate in marketing activities or services provided by a third party, information such as account nickname, profile picture, name, and contact details may be required for the service. We will share your personal information with a third party with your separate consent or when it is necessary for the third party to provide marketing activities or services for you. To ensure that a third party can provide services to you smoothly or deliver rewards to you in a timely manner. If you refuse to share, a third party will be unable to provide you with services or refuse your participation if it is necessary to provide you with marketing activities or service content.
2.2 Transfer
We will not transfer your personal information to any company, organization or individual other than Xi 'an Diance Network Technology Co., LTD., except in the following circumstances:
With your explicit authorization or consent in advance;
To meet the requirements of laws, regulations, legal procedures, or mandatory government requirements or judicial decisions;
If we or our affiliated companies are involved in a transaction such as a merger, division, liquidation, acquisition or sale of assets or business, if it involves the transfer of personal information, we will ensure the confidentiality of such information at the time of transfer and inform you of the name or surname and contact details of the recipient. At the same time, we will require the transferee to process and protect in accordance with the same or higher standards and requirements as this policy; otherwise, we will require the transferee to seek your consent again. In addition, we will anonymize or destroy personal information without a data recipient.
2.3 Public disclosure
We will disclose your personal information publicly only in the following circumstances:
Obtain your separate consent;
Based on laws, regulations, legal proceedings, litigation, or mandatory requirements of government authorities.
When making penalty announcements for offending accounts or violations, we will disclose information about the relevant accounts, which inevitably includes account-related authentication information and violations.
2.4 Exceptions to obtaining prior authorization when sharing, transferring, or publicly disclosing personal information
In the following circumstances, the sharing, transfer or public disclosure of personal information does not require prior authorization and consent from the personal information subject:
Directly related to national security and defense security;
Necessary for the conclusion and performance of a contract in which an individual is a party;
It is necessary to perform legal duties or obligations;
Relating directly to public security, public health, or major public interests. For example: to respond to a public health emergency, or to protect the life, health and property of a natural person in an emergency;
Directly related to criminal investigation, prosecution, trial and enforcement of judgments;
Where it is necessary to safeguard the life, property or other major legitimate rights and interests of the personal information subject or other individuals, but it is difficult to obtain the consent of the individual concerned;
In accordance with the provisions of laws and regulations, within a reasonable scope, personal information that has been disclosed by the individual himself or otherwise lawfully disclosed, such as legitimate news reports, government information disclosure channels, etc
Where otherwise provided by law or administrative regulations.
2.5 Third-party software development kits (SDKS) We access
Hyper MZT is integrated with third-party SDKS in order to adapt to use Hyper MZT and third-party platform services on different mobile devices for your mobile device identity authentication and mobile device security. The third-party SDKS mentioned above are provided by mobile device manufacturers, social media platforms, and telecommunications operators. Some third-party SDKS may invoke your device permissions and obtain your relevant information so that you can use the corresponding functions normally on different mobile devices or third-party platforms. The types of device permissions invoked and the information obtained by different third-party SDKS may vary and may include obtaining your location, reading/writing to your external memory card, reading your phone status and identity, viewing WLAN connections, retrieving running apps/Bluetooth information. Regarding the specific types of device permissions invoked by third-party SDKS and how your personal information is collected and used, it is recommended that you refer to the relevant service agreements and privacy policies of third-party SDKS. If you would like to learn more about the third-party SDKS we have integrated, please read the third-party SDK description.
2.6 Delegated processing and co-processing
In order to better serve you, we may entrust third-party partners to process your personal information. We will only entrust third-party partners to process your information for legitimate, proper, necessary, specific and clear purposes. We will strictly limit the purposes for which the entrusted party processes the information and require the entrusted party to take adequate data security measures. If a third party partner uses your information for purposes not entrusted by us, it will obtain your consent separately. Authorized partners we entrust include those for advertising and analytics services. We entrust these partners to handle information related to AD placement, AD performance, and AD reach, subject to industry-standard security technologies. Among them, in order to identify the click-through effect of ads on smart devices, we may provide advertising partners with the IMEI and OAID of the mobile phone attached to the Hyper MZT APP bound to that device in an encrypted manner. Without your valid authorization, we will not entrust third-party partners to process information that can directly identify your personal identity. If you voluntarily leave your personal information such as contact details and address information for a specific third party partner to contact you, they will process your personal information directly.
In co-processing scenarios, we will also sign relevant agreements with partners in accordance with the requirements of laws and regulations and fulfill relevant obligations for the protection of personal information.
3 How do we store and protect your personal information
3.1 Retention period
We will retain your personal information for as long as necessary to provide the services, except in cases where laws and regulations provide otherwise, you agree to a longer retention period, to ensure the security and quality of the services, to achieve the purpose of dispute resolution, or where it is technically difficult to achieve, after the expiration of the aforementioned retention period, we will extend the retention period in accordance with the law, as agreed, or to a reasonable extent.
Beyond the retention period, we will delete your personal information or anonymize it in accordance with the law.
3.2 Place of Storage
In principle, personal information collected and generated within the territory of the People's Republic of China will be stored within the territory of the People's Republic of China. If your personal information is likely to be transferred to a jurisdiction outside the country/region where you use the product or service, or be accessed from those jurisdictions, we will strictly fulfill the obligations stipulated by laws and regulations and obtain your separate consent in advance as required by law. Such jurisdictions may have different data protection laws or even no relevant laws at all. In such cases, we will transfer your personal information in accordance with the current laws of China and will ensure that your personal information is adequately and equally protected within the territory of the People's Republic of China. For example, we will ask for your consent for the cross-border transfer of your personal information, or implement security measures such as data de-identification before the cross-border data transfer.
3.3 Security measures
We will collect, use, store and transfer user information on the principle of "minimization" and inform you of the purposes and scope of the use of such information through the User Agreement and Privacy Policy.
We attach great importance to information security. We have established dedicated teams to develop and apply a variety of security technologies and procedures, etc. We conduct security background checks for security management leaders and key security positions, and we have established a sound information security management system and internal security incident response mechanism, etc. We will take appropriate security measures and technical means in line with industry standards to store and protect your personal information to prevent it from being lost, accessed, disclosed, used, damaged, lost or leaked without authorization. We will take all reasonable and feasible measures to protect your personal information. We will use encryption technology to ensure the confidentiality of your data; We will use trusted protection mechanisms to prevent data from being maliciously attacked.
We will train and assess our employees on data security awareness and security capabilities to enhance their understanding of the importance of protecting personal information. We will verify the identities of employees who handle personal information and control their access rights. We will also sign confidentiality agreements with employees and partners who have access to your personal information, clearly defining job responsibilities and code of conduct to ensure that only authorized personnel have access to personal information. If there is any violation of the confidentiality agreement, the partnership with Xi 'an Diance Network Technology Co., Ltd. will be immediately terminated and the relevant legal responsibilities will be pursued. Confidentiality requirements will also be imposed on personnel who have access to personal information when they leave their posts.
We remind you that the Internet is not an absolutely secure environment. When you interact with other users through third-party social software, email, text messages, etc. embedded in Hyper MZT with your geographical location or travel trajectory information, it is uncertain whether the third-party software will fully encrypt the transmission of information. Please ensure the security of your personal information.
We also ask you to understand that in the Internet industry, due to technological limitations and rapid development, as well as possible malicious attack methods, even if we do our best to enhance security measures, it is impossible to guarantee 100% security of information all the time. Please be aware that the systems and communication networks you use when using our products and/or services may have security issues in other links beyond our control.
3.4 Notification of Security Incidents
We will develop an emergency response plan for cyber security incidents to deal with security risks such as system vulnerabilities, computer viruses, cyber attacks, and cyber intrusions in a timely manner. In the event of an incident endangering cyber security, we will immediately activate the emergency response plan, take corresponding remedial measures, and report to the relevant authorities as required.
Personal information leakage, damage or loss is a company-level major security incident. We will be responsible for regularly organizing members of the working group to conduct security plan drills to prevent such security incidents from happening. In the event of an unfortunate incident, we will activate the emergency response plan based on the highest priority, form an emergency response team, and trace the cause and minimize the loss as soon as possible.
In the event of an unfortunate personal information security incident, we will, in accordance with the requirements of laws and regulations, promptly inform you of the basic situation and possible impact of the security incident, the measures we have taken or will take to handle it, suggestions for risks that you can independently prevent and reduce, and the remedial measures for you, etc. We will inform you of the relevant circumstances of the incident in a timely manner through in-site notifications, text messages, phone calls, emails or other contact information you have reserved. When it is difficult to inform each individual, we will issue a public announcement through reasonable and effective means. At the same time, we will also proactively report the handling of personal information security incidents as required by regulatory authorities. Please understand that, in accordance with the provisions of laws and regulations, if the measures we have taken can effectively prevent the harm caused by the leakage, tampering or loss of information, we may choose not to notify you of the personal information security incident unless the regulatory authorities require you to be notified.
4. Your rights
In accordance with relevant Chinese laws, regulations, standards, and common practices in other countries and regions, we guarantee that you can exercise the following rights over your personal information. If you have any questions or claims regarding the exercise of these rights, you can also contact us through [8. How to Contact Us] :
4.1 Right to access
In principle, you may access your personal information in the following ways:
Account information: Go to [My] - [Personal Information] to access or edit the profile information in your account.
4.2 Right of Deletion
You may request us to delete your personal information in the following circumstances:
If we process your personal information in violation of laws, regulations or our agreement with you;
If the purpose of our processing has been achieved, cannot be achieved, or is no longer necessary to achieve the purpose of processing;
If we cease to provide the product or service, or the retention period has expired;
If you withdraw your consent;
Other circumstances as prescribed by laws and administrative regulations.
When you remove information from our services, we may not immediately remove the corresponding information from our backup systems, but will remove it when the backup is updated. Please be aware and understand that if the retention period required by law, administrative regulation or this agreement has not expired, or if it is technically difficult to delete your personal information, we will cease processing other than storage and taking necessary security measures.
4.3 Withdrawal of Consent
Each business function requires some basic personal information to be completed. You may give or withdraw your consent at any time for the collection and use of additional personal information collected.
You can directly disable system permissions such as storage, location information, camera, microphone, camera, contacts, etc. in the device system, change the scope of consent, or withdraw your authorization.
When you withdraw your consent, we will no longer be able to provide you with the corresponding services and will no longer use your relevant personal information. But your decision to withdraw consent will not affect the processing of your personal information that was carried out on the basis of your consent.
4.4 Right to cancel
You can log out of your Hyper MZT account by following this path: Hyper - Log Out Account
Once you cancel your Hyper MZT account, you will not be able to use the service, so please proceed with caution. In order to protect your or others' legitimate rights and interests, we will determine whether to support your cancellation request based on your use of the product. Except as required by law, we will cease to provide you with products and services and delete your personal information upon your request after you cancel your account.
4.5 Right to copy and portability
You have the right to copy the personal information we collect about you. You may also request that we transfer your personal information to another entity you have specified, provided that it is technically feasible, in accordance with laws and regulations and in compliance with instructions and conditions set by the Cyberspace Administration of China.
4.6 Be informed in advance of the right to cease the operation of products and services.
Hyper MZT wishes to be with you all the time. If Hyper MZT products cease to operate due to special reasons, we will notify you within a reasonable period on the main page or in-site message of the products or services or by sending you an email or other appropriate means to reach you, and will cease collecting your personal information. At the same time, we will delete or anonymize your personal information that has been collected in accordance with the law.
4.7 The right to be interpreted
You have the right to request an explanation from us regarding our personal information processing rules. You may contact us through the contact information provided in Part 8.
4.8 Exceptions to the exercise of rights
We may not be able to respond to your requests for access, correction and addition, deletion, copy and portability, informed decision in the following circumstances:
Directly related to national security and defense security;
Relating directly to public security, public health, and major public interests;
Directly related to criminal investigation, prosecution, trial and enforcement of judgments, etc.
We have sufficient evidence to show that you are subjectively malicious or abusing your rights (such as your request will endanger public safety and the legitimate rights and interests of others, or your request goes beyond what is generally covered by technical means and commercial costs);
Responding to the request of the personal information subject will cause serious damage to your or other individuals' or organizations' legitimate rights and interests;
Involving trade secrets;
Where otherwise provided by law or administrative regulations.
4.9 How to respond to your claims
For security purposes, you may need to provide a written request or prove your identity in other ways. We may first ask you to verify your identity before processing your request. After verification, we will respond within fifteen business days.
For reasonable requests, we do not charge in principle, but for repeated requests that exceed reasonable limits, we may charge a certain cost fee as appropriate. We may refuse requests that are unjustified, require excessive technical means (for example, require the development of a new system or a fundamental change to current practice), pose a risk to the legitimate interests of others, or are highly impractical.
5. Third-party SDKS
Third-party SDKS will collect your relevant device information at a certain frequency when the product is silent or running in the background, and we have no control over the background operation collection behavior of third-party SDKS. The acquisition and use of such information will follow the privacy policy of the SDK itself, but we will exercise reasonable supervisory obligations.
(a) Google Analytics SDK (com. Google. Firebase. Analytics) to collect information: device identifier (such as IMEI, Android ID and MAC address), used for data about application usage and user interaction analysis. Developers: Google Corporation privacy link: https://policies.google.com/privacy
(b) Firebase Crashlytics SDK (com. Google. Firebase. Crashlytics) to collect information, the device identifier (such as IMEI, Android ID and MAC address), used for application data collection and analysis of collapse. Developers: Google Corporation privacy link: https://policies.google.com/privacy
(c) Microsoft speech recognition SDK (com. Microsoft. Cognitiveservices. Researched) to collect information, the device identifier (such as IMEI, Android ID and MAC address), user's speech input data. It is used to convert the user's voice input to text, providing voice recognition and synthesis capabilities. Developers: Microsoft Corporation privacy link: https://privacy.microsoft.com/en-us/privacystatement
(d) Information collected by Tencent Audio and Video SDK (com.tencent.qcloud), device identifiers (e.g. IMEI, Android ID, MAC address), and accelerometers The accelerometer is used to implement common features in video call scenarios such as two-person audio and video calls, group audio and video calls, calling a third party in the middle, Al call noise reduction, and call lag optimization. The accelerometer is used to obtain the horizontal and vertical screen status of the phone during video calls to adapt the direction of the collected screen. Developers: shenzhen tencent computer systems co., LTD. Privacy link: https://cloud.tencent.com/document/product/1640/80198
6. How do we handle personal information of minors
Xi 'an Diance Network Technology Co., Ltd. attaches great importance to the protection of minors' information.
Our products and services are primarily for adults. We will only process personal information of minors with the consent of their parents or other guardians as permitted by laws and regulations.
If you are a minor under the age of 14, you should ask your parents or other guardians to read this agreement carefully before using Hyper MZT products and services, or read it carefully together under the guardianship and guidance of your parents or other guardians, and use our products and services or provide us with information only with the consent of your parents or other guardians.
If we discover that we have collected personal information of minors under the age of 14 without obtaining verifiable consent from their parents or other guardians in advance, we will take measures to delete the relevant information as soon as possible. If at any time a guardian has reason to believe that we have collected personal information of a minor without the guardian 's consent, please contact us at service@pgyer.com and we will take action to delete the relevant data as soon as possible.
1. If you are a minor under the age of 18, you should, under the guardianship and guidance of your guardian and with the consent of your guardian, carefully read and agree to this agreement before using Hyper MZT software and related services. If you do not obtain the consent of your guardian, the guardian may notify Xi 'an Diance Network Technology Co., Ltd. to handle the relevant account by contacting the customer service contact information officially published by Xi 'an Diance Network Technology Co., LTD. Xi 'an Diance Network Technology Co., Ltd. has the right to restrict the functions and uses of the relevant account, including but not limited to browsing, Posting information, interactive communication, etc.
2 Xi 'an Diance Network Technology Co., Ltd. attaches great importance to the protection of personal information of minors. When minors fill in personal information, please enhance personal protection awareness and handle it carefully, and use Hyper MZT software and related services correctly with the consent of the guardian and under the guidance of the guardian.
3. The minor user and his/her guardian understand and confirm that if you violate the laws and regulations and the contents of this agreement, you and your guardian shall bear all legal responsibilities that may result therefrom in accordance with the law.
4 Xi 'an Diance Network Technology Co., Ltd. provides youth mode specifically for minors, and guardians should choose to use the youth mode for minors.
5 Special tips for Minor users
(1) Minors using Hyper MZT software and related services should, under the supervision and guidance of their guardians, learn to use the Internet correctly within a reasonable range, avoid being addicted to virtual cyberspace, and develop good online habits;
(2) Teenage users must abide by the National Convention on Internet Civilization for Teenagers;
(3) Be good at learning online and do not browse bad information;
(4) Communicate honestly and amicably, and do not insult or deceive others;
(5) Enhance self-protection awareness and do not casually date online friends;
(6) Maintain online security and do not disrupt online order;
(7) It should be beneficial to physical and mental health and not be addicted to the virtual world.
6. To better protect the privacy rights of minors, Xi 'an Diance Network Technology Co., Ltd. particularly reminds you to be cautious when publishing content containing materials of minors. Once published, it is deemed that you have obtained the consent of the rights holder to display the portrait, voice and other information of minors in Hyper MZT software and related services, And you permit Xi 'an Diance Network Technology Co., Ltd. to use and process such content related to minors in accordance with this agreement.
7 Special Notice from the guardian
(1) If your ward uses Hyper MZT software and related services, you, as the guardian, should guide and supervise the registration and usage behavior of the ward. If your ward applies to register a Hyper MZT account, Xi 'an Diance Network Technology Co., Ltd. will have the right to consider that it has obtained your consent;
7. Revision of the Privacy Policy
Our privacy policy may change.
We will not reduce the rights you are entitled to under this agreement without your explicit consent. We will post any changes made to this agreement on this page.
For material changes, we will notify you on the main exposure page of the product or service or in an in-site message or by sending you an email or any other appropriate means to reach you. If you do not agree with such changes, please stop using Hyper MZT products and services immediately.
Material changes referred to in this agreement include, but are not limited to:
There are significant changes to our service model. Such as the purposes for which personal information is processed, the types of personal information processed, how personal information is used, etc.
We have significant changes in ownership structure, organizational structure, etc. Such as changes in ownership resulting from business adjustments, bankruptcies, mergers and acquisitions, etc.
Changes in the main objects to which personal information is provided, transferred or disclosed publicly;
There are significant changes in your rights to participate in the processing of your personal information and the ways to exercise them;
When the department responsible for personal information security, contact information and complaint channels change;
When the personal information security impact assessment report indicates a high risk.
8. How to contact us
The growth of Hyper MZT is inseparable from the joint efforts of all user experts, and we are very grateful for your contributions to Hyper MZT data updates and usage feedback.
You can contact us by sending an email to service@pgyer.com.
To ensure our efficient handling of your issue and prompt feedback to you, you need to submit identification, valid contact information, a written request and relevant evidence, and we will verify your identity to process your request.
Attached: Explanations of terms
Personal information refers to all kinds of information recorded in electronic or other forms that are related to identified or identifiable natural persons, excluding information that has been anonymized. Personal information includes names, dates of birth, identification numbers, personal biometric information, addresses, communication contact information, communication records and contents, account passwords, property information, credit information, travel records, accommodation information, health and physiological information, transaction information, etc.
Sensitive personal information refers to personal information that, once leaked or illegally used, is likely to cause harm to the dignity of a natural person or to their personal or property safety, including biometric information, religious beliefs, specific identities, medical health, financial accounts, travel records, and personal information of minors under the age of 14.
Devices refer to devices that can be used to access Hyper MZT products or services, such as desktop devices, tablets or smartphones.
Device information may include device attribute information (such as hardware model, operating system version and system status, device configuration) of the terminal device you use to install and run the Hyper MZT SDK International Mobile Equipment Identity (IMEI), International Mobile User Identification (IMSI), Network Device Hardware Address (MAC), Advertising Identifier (IDFA), Vendor Identifier (IDFV), Mobile Device Identification (MEID), Anonymous Device Identifier (OAID), Integrated Circuit Card Identification (ICCID), Android Device identifiers such as ID and hardware serial number, device connection information (such as browser type, telecom operator, language used, WIFI information), and device status information (such as device application installation list).
Log information refers to the requests that our servers automatically record when you access Hyper MZT, Such as your IP address, the type and language of your browser, information about your hardware device, version of your operating system, information about your network operator, the date, time, duration of your access to the service, and other information that you provide, form, or retain while using our products or services.
Location information refers to precise location information obtained through GPS information, WLAN access points, Bluetooth, base stations, and other sensor information, as well as rough geographical location information obtained through IP addresses or other network information.
De-identification is the process by which personal information is processed so that it cannot be used to identify a particular natural person without additional information.
Anonymization is the process of technical processing of personal information so that the subject of the personal information cannot be identified and the processed information cannot be restored. Personal information obtained through anonymization does not fall under the category of personal information.
Associated companies refer to Xi 'an Diance Network Technology Co., LTD., the operator of Hyper MZT, and other associated companies either individually or collectively. "Associated relationship" refers to any entity (including individuals, companies, partnerships, organizations, or any other entity) which is directly or indirectly controlled by it, or which is directly or indirectly controlled by it, or which is directly or indirectly controlled by the same entity. The "control" referred to here means having, by holding a vote, contract, or otherwise, the power to direct or indirectly give instructions or direct others to give instructions regarding the management and decision-making of the relevant entity, or any other relationship that actually constitutes actual control.
Thank you again for your trust and use of Hyper MZT!
Xi 'an Diance Network Technology Co., LTD
July 7, 2025